We have sent instructions to your email
Thank you! Now, prove the ownership.
Upon giving your email you will get detailed instructions of how to provide proofs that you actually own this website.
Hacken’s automated security scanner provides the highest level of detection of over 6,800 vulnerabilities with nearly 0% false positives. With our solution, you can check your website in just a few clicks and be sure of the highest security level of your web infrastructure.
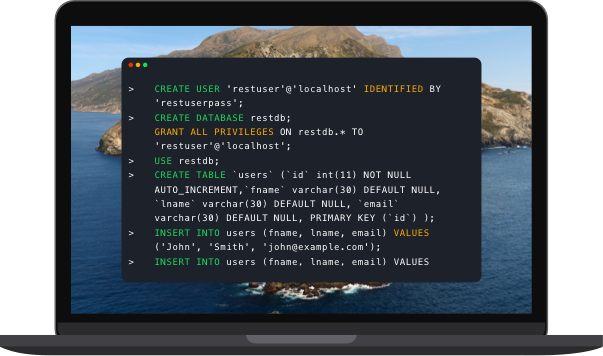

The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.

Application functions related to authentication and session management are allowing attackers to compromise passwords.

Attackers may steal or modify the weakly protected data to carry out credit card fraud, identity theft, or other crimes.

External entities can be used to disclose internal files using the file URI handler, internal file shares, internal port scanning, remote code execution, and denial of service attacks.

Attackers can exploit these flaws to access unauthorized functionality and/or data such as other users’ accounts, view sensitive files, modify other users’ data, change access rights, etc.

All operating systems, frameworks, libraries, and applications have to be securely configured as well as patched/upgraded in a timely fashion.

XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.

Insecure deserialization often leads to remote code execution.

If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover.

Most breach studies show that time to detect a breach is over 200 days and the breach is typically detected by external parties rather than internal processes or monitoring.
Please provide URL of the website you want to check.
Add TXT record to your DNS records to prove that this website is yours.
We will prepare your risk assessment report in 24 hours.
Finds common vulnerabilities which affect web applications: SQL Injection, XSS, OS Command Injection, Directory Traversal, and others. The scanner also identifies specific web server configuration issues.
Speed-up your penetration test with this online scanner. It is already set-up and configured with the optimal settings for best results and performance. Just start the scanning and come back later for results.

You can perform a self-security assessment to detect weaknesses in your own application. This will allow you to fix the vulnerabilities before being hit by real attackers.

If you are a web development company, you can show this report to your clients and prove that you have implemented the proper security measures in the application.
At Hacken, we are always working on improving the utility of our Hacken Token (HAI). We have made it available to purchase one of the best solutions for security scanning with our native HAI tokens.









Upon giving your email you will get detailed instructions of how to provide proofs that you actually own this website.